2016 saw ransomware run rampant across the globe, with more sophisticated attacks than ever before. Changes to ransomware variants now include total disk encryption as well as network aware scanning able to target shares on remote computers. A report by Kasperksy labs for 2016 has seen the main focus on ransomware variants throughout the year far exceeding any other form of attack with the focus on businesses.
The number speak for themselves
- 62 new ransomware variants made their appearance
- There was an 11-fold increase in the number of ransomware modifications, from 2,600 new modifications in the first quater to 32,091 in the third quater of 2016
- Attacks on business increases three-fold between January and September, the difference between every attack from one every 2 minutes to one every 40 seconds
- For individuals the rate of increase went from every 20 seconds to every 10 seconds
- One in five business who paid the ransom never got their data back
Growth in sophistication
2016 saw ransomware grow in sophistication for example: changing tactics if it encountered financial software, written in scripting languages and exploiting new infection paths, becoming more targeted, and offering turn-key ransomware-as-a-service solutions to those with fewer skills, resources or time through an underground ecosystem.
The fight back
In July the No More Ransom project was launched, bringing together law enforcement agencies, Intel Security and Kaspersky Labs. 13 more organizations joined in October. Among other things, the collaboration has resulted in a number of free online decryption tools that have help tens of thousands ransomware victims recover their precious data.
What is ransomware.
Ransomware comes in two forms. The most common form of ransomware is the cryptor. These programs encrypt data on the victim’s device and demand money in return for a promise to restore the data. Blockers, by contrast, don’t affect the data stored on the device. Instead, they prevent the victim from accessing the device. The ransom demand, displayed across the screen, typically masquerades as a notice from a law enforcement agency, reporting that the victim has accessed illegal web content and indicating that they must pay a spot-fine. You can find an overview of both forms of ransomware here.
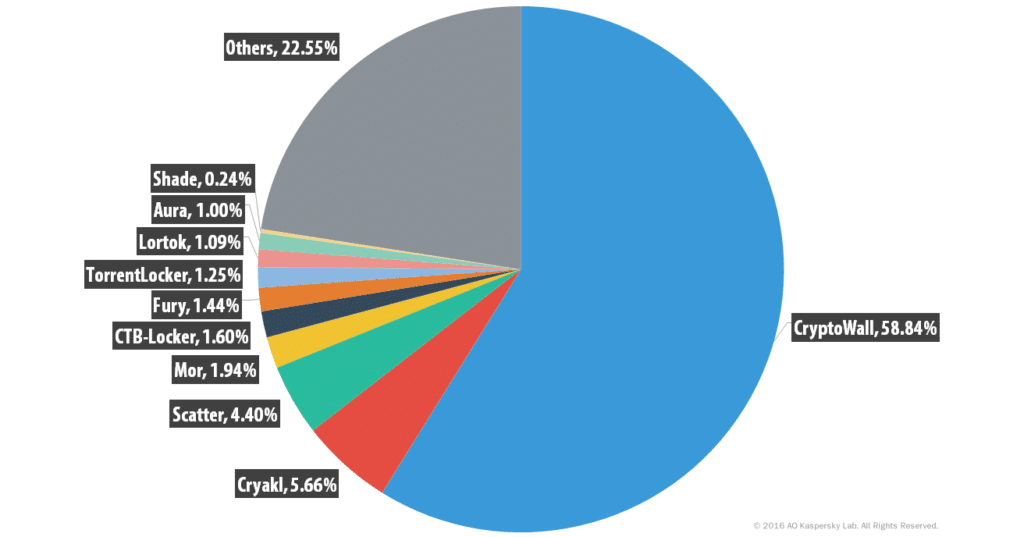
As of October 2016, the top ransomware families detected by Kaspersky Lab products look like this:
| Name | Verdicts* | percentage of users** | |
| 1 | CTB-Locker | Trojan-Ransom.Win32.Onion / Trojan-Ransom.NSIS.Onion | 25.32 |
| 2 | Locky | Trojan-Ransom.Win32.Locky / Trojan-Dropper.JS.Locky | 7.07 |
| 3 | TeslaCrypt (active till May 2016) | Trojan-Ransom.Win32.Bitman | 6.54 |
| 4 | Scatter | Trojan-Ransom.Win32.Scatter / Trojan-Ransom.BAT.Scatter / Trojan-Downloader.JS.Scatter / Trojan-Dropper.JS.Scatter | 2.85 |
| 5 | Cryakl | Trojan-Ransom.Win32.Cryakl | 2.79 |
| 6 | CryptoWall | Trojan-Ransom.Win32.Cryptodef | 2.36 |
| 7 | Shade | Trojan-Ransom.Win32.Shade | 1.73 |
| 8 | (generic verdict) | Trojan-Ransom.Win32.Snocry | 1.26 |
| 9 | Crysis | Trojan-Ransom.Win32.Crusis | 1.15 |
| 10 | Cryrar/ACCDFISA | Trojan-Ransom.Win32.Cryrar | 0.90 |
* These statistics are based on the detection verdicts returned by Kaspersky Lab products, received from usersof Kaspersky Lab products who have consented to provide their statistical data.
** Percentage of users targeted by a certain crypto-ransomware family relative to all users targeted with crypto-ransomware.
Why bother with a file when you can have the disk?
- New approaches to ransomware attacks that were seen for the first time in 2016 included disk encryption, where attackers block access to, or encrypt, all the files at once. Petya is an example of this, scrambling the master index of a user’s hard drive and making a reboot impossible. Another Trojan, Dcryptor, also known as Mamba, went one step further, locking down the entire hard drive. This ransomware is particularly unpleasant, scrambling every disk sector including the operating system, apps, shared files and all personal data – using a copy of the open source DiskCryptor software.
- The ‘manual’ infection techniqueDcrypter’s infection is carried out manually, with the attackers brute-forcing passwords for remote access to a victim machine. Although not new, this approach has become significantly more prominent in 2016, often as a way to target servers and gain entry into a corporate system.If the attack succeeds, the Trojan installs and encrypts the files on the server and possibly even on all the network shares accessible from it. We discovered TeamXRat taking this approach to spread its ransomware on Brazilian servers.
- Two-in-one infectionIn August we discovered a sample of Shade that had unexpected functionality: if an infected computer turned out to belong to financial services, it would instead download and install a piece of spyware, possibly with the longer term aim of stealing money.
Shade downloaded spyware if it found financial software #KLReport
For some tips on how to help protect yourself and your data see Ransomware – Prevention of data loss